CWNA Chapter 17: 802.11 Network Security Architecture
Today we are going to discuss 802.11 Network Security as we review CWNA Chapter 17. Honestly before reading this chapter I took wireless security for granted, not understand how complex the underlying technology was. It was quite eye opening to see how it works under the hood. Please pay close attention to the 4-Way Handshake as it is very important to understand for this exam.
802.11 Security Basics
5 Major Components
- Data privacy and integrity
- Authentication, authorization, and accounting (AAA)
- Segmentation
- Monitoring
- Policy
Data privacy and integrity
Due to wireless transmissions being available to anyone in listening range, using cipher encryption technologies to obscure information is mandatory to provide proper data privacy. A cipher is an algorithm used to perfrom encryption. The two most common ciphers used to protect data are ARC4 algorithm and Advanced Encryption Standard (AES) algorithm. Some ciphers encrypt data in a continuous stream, whereas others encrypt data in blocks.
ARC4 Cipher: streaming cipher used to protect 802.11 wireless data in two legacy encryption methods, known as WEP and TKIP. It is short for Alleged RC4.
Advanced Encryption Standard Cipher: AES is a block cipher that offers much stronger protection than the ARC4 streaming cipher. AES uses an encryption method known as Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP). Isn’t CCMP so much easier to say? AES encrypts data in fixed data blocks with choices in encryption key strengths of 128, 192, or 256 bits. It is mandated for use in the US government for protecting sensitive and classified information. AES is commonly used in other technologies like IPSec VPNs.
WEP, TKIP and CCMP all use data integrity checks to ensure that the data has not been altered. WEP uses an integrity check value (ICV), and TKIP uses a message integrity check (MIC). CCMP also used a MIC that is much stronger than the data integrity methods used in TKIP and WEP.
Authentication, Authorization, and Accounting (AAA)
AAA is a key computer security concept that defines the protection of network resources.
Authentication: Authentication is the verification of identity and credentials. Users or devices must identify themselves and present credentials, such as usernames and passwords or digital certificates.
Authorization: Authorization determines if the device or user is authorized to have access to network resources. This can include identifying whether you can have access based upon the type of device you are using (laptop, tablet, smartphone), time of day restrictions, or location.
Accounting: Accounting is the tracking of use of network resources by users and devices. Accounting is used to keep a historical trail of who used what resource, when, and where.
Segmentation
Segmentation is the chosen method of separating user traffic within a network. It is still important to separate users and devices into proper groups, much like what is done on any traditional network. Segmentation can be achieved through a variety of means, including firewalls, routers, VPNs, VLANs, and encapsulating or tunneling techniques, such as Generic Routing Encapsulation (GRE). The most common segmentation used in 802.11 is done by using virtual lans (VLANs). Additionally, segmentation is also used with role-based access control (RBAC).
Monitoring and Policy
It is important to monitor your wireless network to ensure it is working as expected as well as to monitor for attacks and intrusions. This is where the Wireless Intrusion Prevention System (WIPs), discussed in Chapter 16 comes into play.
Legacy 802.11 Security
Legacy Authentication
The original standard specified two methods of authentication: Open System Authentication and Shared Key authentication. These authentication methods were verification between the two devices that they are both valid 802.11 devices.
Open System Authentication: OSA provides authentication without performing any type of user verification. It is a two-way exchange between the client radio and the AP.Client sends an authentication request (no credentials).
1) Client sends an authentication request (no credentials)
2) AP then sends an authentication response
Shared Key: Shared Key uses Wired Equivalent Privacy (WEP) to authenticate client stations and requires that a static WEP key be configured on both the station and the AP. Authentication would not work if the static WEP keys didn’t match. Shared Key authentication was a four-way authentication frame handshake.
Shared Key Process
1) Client station sends an authentication request to the AP.
2) AP sent a cleartext challenge to the client station in an authentication response.
3) Client station encrypted the cleartext challenge and sent it back to the AOP in the body of another authentication request frame.
4) The AP decrypted the stations response and compared it to the challenge text.
1) If they matched, the AP would respond by sending a fourth and final authentication frame to the station confirming success.
2) If they did not match, the AP would respond negatively. Additionally, if the AP could not decrypt the challenge, it would also respond negatively.
If the Shared Key authentication was successful, the same static WEP used initially would also be used to encrypt the 802.11 data frames.
Static WEP Encryption: Wired Equivalent Privacy (WEP) is a layer 2 encryption method that uses the ARC4 streaming cipher. It supports 64 & 128 bit encryption. The three main goals of WEP encryption are:
1) Confidentiality: the aim is to provide data privacy by encrypting the data before transmission.
2) Access Control: this is basically a crude form of authorization. Clients that do not have the same matching static WEP key as an AP are refused access to network resources.
3) Data Integrity: A data integrity checksum known as the integrity check value (ICV) is computed on data before encryption and used to prevent data from being modified.
WEP Process
1) WEP runs a cyclic redundancy check (CRC) on the plaintext data that is to be encrypted and then appends the integrity check value to the end of the plaintext data.
2) A 24-bit cleartext initialization vector (IV) is then generated and combined with the static secret key.
3) WEP then uses both the static key and the IV as seeding material through a pseudorandom algorithm that generates random bits of data know as a keystream.
4) They pseudorandom bits in the keystream are then combined with the plaintext data bits by using a Boolean XOR process. The end result is the WEP ciphertext, whic is the encrypted data.
5) The encrypted data is then prefixed with the cleartext IV.
WEP is quite weak. The following are four main attacks:
1) IV Collision Attack: An attacker can easily recover the secret key when IV collisions occur in WLANs. This will happen at some point because the 24-bit IV is clear text and is different in every frame. We hae to keep in mind there are only 16 million IVs, so they will repeat themselves at some point.
2) Weak Key Attack: Because of the ARC4 key-scheduling algorithm, weak IV keys are generated. An attacker can recover the secret key much easier by recovering the know weak IV keys
3) Reinjection Attack: Hacker tools exist that implement a packet reinjection attack to accelerate the collection of weak IVs on a network with little traffic.
4) Bit-Flipping Attack: The ICV data integrity check is considered weak. WEP encrypted packets can be tampered with.
MAC Filters
MAC filters can be configured to either allow or deny traffic from specific client MAC addresses to associate and connect to an AP. Most vendors use MAC filtering to deny client associations to an AP. Some other vendors use MAC firewall filters to only allow certain clients to pass through the virtual port of the AP and onto the DS. We have mentioned tin the previous chapters that mACs can be spoofed, making MAC filters not completely reliable. IF your legacy devices do not support stranger stronger security, then it would be wise to segment them into their own VLAN, with a MAC filter based on the manufactures OUI.
SSID Cloaking
APs often have a setting called closed network, hidden SSID, or stealth mode. When enabled you can hide or cloak your wireless network name. When implemented, the SSID field in the beacon frame is null, and therefore passive scanning will not reveal the SSID to client stations that are listening to the beacons. APs will respond to directed probe requests from clients that transmit directed probe requests with the properly configured SSID. In the end, anyone with a layer 2 wireless protocol analyzer can capture the frames transmitted by any legitimate end user and discover the SSID, which is transmitted in clear text. The recommendation stands to just broadcast your SSID as cloaking is more of a hassle than it is worth.
Robust Security
The 802.11-2016 standard defines an enterprise authentication method as well as a method of authentication for home use. These methods are 802.11X/EAP and also the use of a pre-shared key or passphrase. The 802.11-2016 standard also requires the use of strong dynamic encryption-key generation methods. CCMP/AES encryption is the default encryption method, and TKIP/ARC4 is an optional encryption method.
Robust Security Network
The 802.11-2016 standard defines what are known as robust security network (RSN) and robust security network associations (RSNAs). Two stations must authenticate and associate with each other, as well as create dynamic encryption keys through a process know as the 4-way handshake. CCMP/AES is the mandated encryption method. A RSN is a network that only allows for the creation of robust security network associations.
Authentication and Authorization
PSK Authentication
The 802.11-2016 standard defines authentication and key management (AKM) services. AKM services require both authentication processes and the generation and management of encryption keys. An authentication and key management protocol (AKMP can be either a pre-shared (PSK) or an EAP protocol used ruing 802.1X/EAP authentication. 802.1X/EAP requires a RADIUS server. WPA/WPA2-Personal uses PSK authentication while WPA/WPA2-Enterprise uses the 802.1X/EAP authentication solution. WPA-Personal is suggested for SOHO environments. WPA/WPA2-Personal also allows an end user to enter a simple ASCII character string, dubbed a passphrase, any length from 8-63 characters is size. In the back end, a passphrase-to-PSK mapping function converts the passphrase to a 256-bit PSK. The 256-bit PSK is used as the pairwise master key (PMK) in the 4-way handshake in 802.1X/EAP. WPA-Personal uses TKIP/ARC4, only supported in older 802.11a/b/g radios. WPA2-Personal uses CCMP/AES.
Proprietary PSK Authentication
Some vendors support the ability for each STA to have their own unique PSK on an SSID using WPA2-Personal. This is done by mapping the MAC of each STA to a unique WPA/WPA2-passphrase. A database of unique PSKs to usernames or client stations must be stored on all access points or on a centralized management server. This helps mitigate social engineering and brute force attacks.
Use cases:
1) Legacy devices
2) Personal devices
3) Guest Access
4) IoT devices
Simultaneous Authentication of Equals
In the 802.11s-2011 amendment a new peer-to-peer authentication method called Simultaneous Authentication of Equals (SAE) was introduced. SAE is based on a Dragonfly key exchange, which is a patent free and royalty-free technology that uses a zero-knowledge proof key exchange, which means a user or device must prove knowledge of a password without having to reveal a password. The goal of SAE is to protect dictionary attacks altogether. SAE is a more secure PKS authentication method, using its protocol exchange to protect teh passphrase from the mentioned brute-force dictionary attacks. SAE has been proposed by the WiFi Alliance as an eventual replacement for PSK authentication as part of the recently announced WPA3 certification.
802.1X/EAP Framework
802.1X/EAP provides an authorization framework that allows or disallows traffic to pass through a port and thereby access network resources. This can be done in either a wireless or wired environment.
802.1X consists of 3 main components:
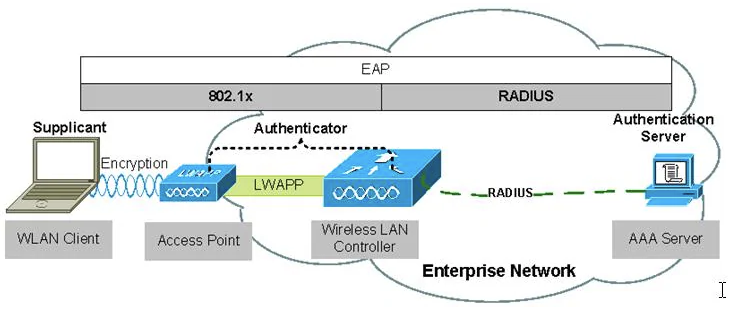
1) Supplicant: a host with software that requests authentication and access to network resources. In a WLAN the supplicant is often the laptop or wireless handheld device trying to access the network.
2) Authenticator: an authenticator device blocks traffic or allows traffic to pass through its port entity. Authentication traffic is normally allowed to pass through the authenticator, while all other traffic is blocked until the identity of the supplicant has been verified. In a WLAN the authenticiator is usually an AP or a WLAN controller.
3) Authentication Server: an authentication server (AS) validates the credentials of the supplicant that is requesting access and notifies the authenticator that the supplicant has been authorized. The AS maintains a native database or may proxy query with an external database, such as an LDAP database, to authenticate a supplicants credentials. A RADIUS server normally functions as the authentication server.
In order for the above to function, an authentication protocol is needed to perform the authentication process. Extensible Authentication Protocol (EAP) is used to provide user authentication. The authenticator allows the EAP traffic to pass through its virtual uncontrolled port. After the authentication server has verified the credentials of the supplicant, the server sends a message to the authenticator that the supplicant has been authenticated The authenticator is then authorized to open the virtual controlled port and allow all other traffic to pass through.
EAP Types
EAP is a layer 2 protocol, with many different flavors like Cisco’s Lightweight Extensible Authentication Protocol (LEAP) which is proprietary. We also have Protected Extensible Authentication Protocol (PEAP) which is considered standards-based. The client must authenticate the server just as the server must authenticate the client. Most types of EAP that require mutual authentication use a server side certificate to validate the authentication server. This creates an encrypted Secure Socket Layer (SSL)/Transport Layer Security (TSL) tunnel in which the supplicants username/password credentials or client certificate can be exchanged.
Dynamic Encryption-Key Generation
Mutual authentication is required to generate unique dynamic encryption keys. The biggest advantage of dynamic encryption keys is that they cannot be compromised by social engineering attacks, because the user has no knowledge of the keys. Additionally every user has a unique key, so none of the other users would be at risk if a single user was compromised.
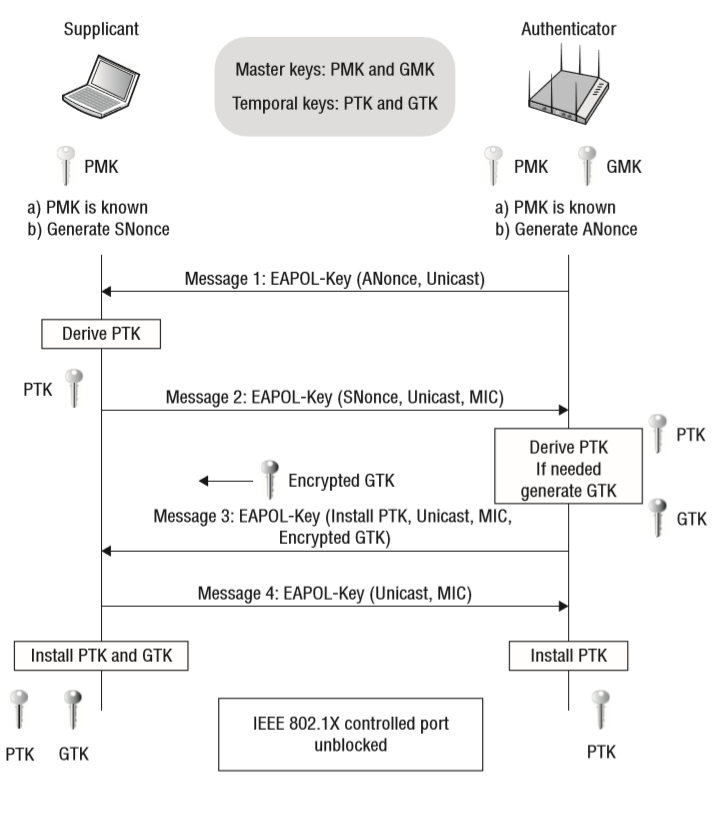
4-Way Handshake
A pairwise master key (PMK) is used to seed the 4-way handshake that generates the unique dynamic encryption keys employed by any two 802.11 radios. The PMK is generated as a by-product of either PSK or 802.1X/EAP authentication. Part of the robust security network association (RSNA) process involves the creation of two master keys, known as the group master key (GMK) and the pairwise master key (PMK). The GMK and PMK are the seeding material used to create the final dynamic keys that are used for encryption and decryption. The final encryption keys are knows as the pairwise transient key (PTK) and hte group temporal ky (GTK). The PTK is used to encrypt/decrypt unicast traffic, and the GTK is used to encrypt/decrypt broadcast and multicast traffic. The 4-way handshake will always be the final four frames exchanged during either an 802.1X/EAP authentication or a PSK authentication. Every time a client radio roams from AP to another, a new 4-way handshake must occur, which will result in new dynamic keys being generated.
WLAN Encryption
802.11-2016 standard defines four encryption methods that operate at layer 2: WEP, TKIP, CCMP, and GCMP. These protect data found in layers 3-7. Not all 802.11 frames are encrypted. 802.11 management frames only carry layer 2 payload in thier frame body. Management frames can be protected, however only if management frame protection (MFP) is enabled. 802.11 control frames only have a header and trailer, so encryption is not necessary. Only 802.11 data frames within an MSDU payload can be encrypted with WEP, TKIP or CCMP. WEP and TKIP use the ARC4 cipher and CCMP and GCMP use the AES cipher.
TKIP Encryption
Temporal Key Integrity Protocol (TKIP) is the optional encryption method defined for a robust security network. TKIP uses the ARC4 cipher like WEP, but is an enhancement that addresses many of the known weaknesses of WEP. TKIP starts with a 128-bit temporal key, which is combined with a 48-bit initialization vector (IV) and source and destination MAC address in a complicated process known as per-packet key mixing. As of the 802.11-2016 standard, WEP and TKIP are not permitted for use in high throughput (HT) or very high throughput (VHT) data rates.
CCMP Encryption
CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) is the default encryption method defined under the 802.11i amendment. CCMP uses Advanced Encryption Standard (AES) algorithm. CCMP/AES uses a 128-bit encryption key size and encrypts in 128-bit fixed length blocks. An 8-byte message integrity check (MIC) is also used, which is much stronger than TKIP.
GCMP Encryption
In the 802.11ad-2012 amendment, the use of Galois/Counter Mode Protocol (GCMP) using AES was standardized. This was brought about due to the high speed requirements of 802.11ad. GCMP is more efficient than CCMP and uses either a 128-bit or 156-bit AES key, where CCMP only uses a 128-bit. Currently no one is using GCMP, as it is not backward compatible with existing WiFi equipment.
Traffic Segmentation
Segmentation can be achieved through a variety of ways, including firewalls, routers, VPNs, and VLANs. Segmentation is often used with role-based access control (RBAC).
VLANs
VLANs are used to create separate broadcast domains in a layer 2 networks and are often used to restrict access to network resources without regard to physical topology of the network. In a WLAN controller model, most user traffic is centrally forwarded to the controller from the APs. The user VLANs are still available ot the wireless users because all the user VLANs are encapsulated in an IP tunnel between the controller-based APs at the edge and the controller in the core. The non-controller model requires support for multiple user VLANs at the edge. Each AP is connected to an 802.1Q trunk prot on an edge switch that supports vlan tagging. All the user VLANs are configured in the access switch. The user VLANs are tagged in the 802.1Q trunk and the wireless user traffic is forwarded at the edge of the network.
Guest SSID/VLAN: When implementing an open SSID, you should still restrict guest users via a firewall policy. Guest users should be denied access to local network resources and routed off to an internet gateway.
Voice SSID/VLAN: The voice SSID might be using a security solution like WPA2 Passphrase, and the VoWiFi client traffic is typically routed to a VOIP server of PBX.
Employee SSID/VLAN: The employee SSID uses stronger security solutions, like WPA2-Enterprise, and ACLs or firewall policies to allow access to internal resources.
RBAC: Role-based access control (RBAC) is an approach to restricting system access to authorized users. The three main roles are users, roles, and permissions. Traffic permissions can be based on layer 2 permissions (MAC Filter), VLANs, layer 3 permissions (access control lists), layers 4-7 permissions (stateful firewall rules), and bandwidth permissions. The user authenticates via 802.1X/EAP, then RADIUS attribute value pairs (AVPs) can be used to assign users to a specific role automatically. Even though they are on the same SSID, they can have differing roles assigned. These roles have traffic permissions that are now allocated to the user.
WPA3
WiFi Protected Access 3 defines enhancements to the existing WPA2 security capabilities for 802.11 radios. New capabilities for both personal and enterprise networks have been announced:
SAE: WPA3 defines stronger authentication with Simultaneous Authentication of Equals (SAE). SAE uses a zero-knowledge proof key exchange, which means a user or device must prove knowledge of a password without having to reveal a password.
MFP: WPA3 defines mandatory support for management frame protection (MFP) as a safeguard against many of the more common layer 2 DoS attacks.
CNSA: WPA3 defines an optional 192-bit cryptographic security suite aligned with the Commercial National Security Algorithm (CSNA) suite.
The following two items were to be part of WPA3 but were later given their own certifications by the WiFi Alliance.
Easy Connect: Defines simplified on boarding security with a new Device Provisioning Protocol (DPP). The goal is to simplify the configuration of devices with limited or no display.
Enhanced Open: Defines improved data privacy in open networks using a protocol called Opportunistic Wireless Encryption (OWE). The goal here is to improve security at open WiFi hotspots. OWE will define methods to provide each WiFi hotspot user with an individual encryption key without any required authentication.
VPN Wireless Security
VPNs are not normally recommended to provide wireless security in the enterprise due to the overhead and because faster layer 2 solutions are now available. VPNs would typically be used when using public WiFi hotspots. This should be mandatory for employees using work laptops.
VPN 101
A VPN is essentially a private network that is created or extended across a public network. In order for a VPN to work, two computers or devices communicate to establish what is known as a VPN tunnel. Typically a VPN client initiates the connection by trying to communicate with the VPN server. The VPN client can be a computer, router, WLAN controller, or even an AP.
Steps:
1) When the client and server are able to communicate with each other, the client will attempt to authenticate with the server by sending its credentials.
2) The server will take the clients credentials and validate them. If valid, the server and client will create the VPN tunnel between them.
3) From this moment on, all traffic sent through the tunnel is encrypted.
Layer 3 VPNs
VPNs use secure tunneling, which is the process of encapsulating on IP packet within another IP packet. The original destination and source IP address of the first packet are encrypted along with the data payload of the first packet. The IP address of the second or outer packet are seen in clear text and are used for communications between the tunnel endpoints. The destination and source IP addresses of the second packet will point to the public IP address of the VPN server and VPN client. The most commonly used layer 3 VPN technology is Internet Protocol Security (IPSec). IPSec VPNs user stronger encryption methods and more secure methods of authentication.
SSL VPNs
Unlike an IPSec VPN, an SSL VPN does not necessarily require the installation and configuration of client software on the end users computer. A user can connect to a Secure Sockets Layer (SSL) VPN server via a web browser. The traffic between the we browser and the SSL VPN is encrypted with the SSL protocol or Transport Layer Security (TLS).
Chapter Review
In CWNA Chapter 17, we discussed many different forms of authentication as well as how they function. From this chapter you should take away the differences between TKIP/ARC4 and CCMP/AES, the differences between WPA and WPA2, 802.1X/EAP process, the 4-way handshake. Knowing those key areas are critical to your understanding of wireless security as well as passing this exam. In the end that is our goal! Please pay close attention to the blueprint laid out Here at CWNP.com. Security is 10% of the exam, so know out of 60 questions, you would imagine at least six are on security.
Interesting link of the day
This isn’t so much of a link as it a community that you can join if you are a WiFi professional. The first assumption is that you have a Twitter account. Assuming you do, you can reach out to @samuel_clements and ask for permission to join the Wi-Fi Pros Slack group. It is filled with tons of WiFi industry names that are willing to help you out if you have something you are having trouble with, or just a simple question. That is all for now. Look for the next chapter soon!

















