CWNA Chapter 18: Bring Your Own Device (BYOD) and Guest Access
Today we are going to dive into BYOD devices on the corporate network and how we manage them. In the last chapter we discussed wireless security, which was a great primer for this chapter. As you already know, there are many more personally owned devices on networks in which they are allowed, than there are corporate provided ones. This brings with it a level of risk that needs to be mitigated somehow. This is where we get into Mobile Device Management and guest management.
Mobile Device Management
An MDM solution can manage devices across multiple mobile operating systems and across mobile service providers. The main focus of an MDM is the management of smartphones and tablets, however some MDM solutions can also be used to onboard personal MAC OS and Chrome OS laptops.
MDM Solutions Vendors
- VMWare AirWatch
- Citrix
- IBM
- JAMF Software
- Mobile Iron
Company-Issued Devices Vs. Personal Devices
Company issued devices usually entails more in depth security due to sensitive corporate documents and information stored on them. Company devices are normally provisioned with VPN access, email, WiFi profile settings, passwords, and encryption settings. Remote wiping is enabled to protect against stolen data, should a device be lost or stolen. Additionally, the IT department can decide what applications can be installed on a device. When BYOD devices are brought into the corporate environment, it is possible to do something like disable the camera to protect sensitive trade secrets from being photographed on a cell phone. As an alternative to MDM, NAC (network access control) can be used to authenticate personal devices along with controlling access to the enterprise network without having to install software on the client. NAC solutions cannot control the client, but can dictate the level of access the personal device has on the network.
MDM Architecture
MDM solutions consist of the following four main components:
- Mobile Device: This can be a corporate or personal owned mobile device. Mobile devices cannot access the network until an enrollment process has been completed and an MDM profile has been installed.
- AP/WLAN Controller: If the devices have not been enrolled via the MDM server, then the AP or WLC quarantines the mobile device within a restricted area of the network know as a walled garden.
- MDM server: The MDM server is responsible for enrolling clients and provisioning the client with an MDM profile. Certificates can also be provisioned from the MDM server. Additional tasks can also include client device monitoring, and device inventory control and configuration.
- Push Notification Servers: MDM server communicates with push notification servers such as Apple Push Notification service (APNs) and Google Cloud Messaging (GCM), for over the air management of mobile WiFi devices.
MDM Enrollment
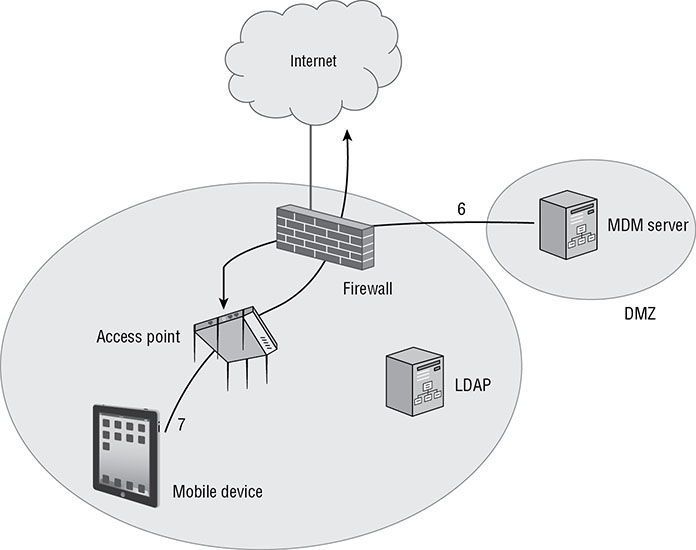
Mobile devices must go through the following steps when MDM architecture is in place:
- The mobile device connects with the AP: at first association with the AP, the client is put in a “walled garden”, limiting access to network resources other than DHCP, DNS, push notification services, and the MDM server.
- The AP checks whether the device is enrolled: the AP or WLC now queries the MDM server to determine the enrollment status of the mobile device. If the MDM is cloud based it traverses the WAN, if local it is typically in a DMZ. If already enrolled, the MDM will communicate that to the AP and the mobile device will be released from the walled garden. If not enrolled, we continue.
- The MDM server queries LDAP: the MDM server queries an existing LDAP database, such as AD (active directory), then the LDAP server responds, allowing the MDM enrollment to continue.
- The device is redirected to the MDM server: at this point the mobile device will be redirected to a captive web portal, where the user will be asked to agree to legal disclaimers that detail what restrictions will be placed on the device. If they do not agree, they will not get released from the walled garden.
- The device installs the certificate and MDM profile: once enrollment begins, a secure over the air provisioning process for installing the MDM profile is needed.
- The MDM server releases the mobile device: once the device has completed the MDM enrollment, the MDM server sends a message to the AP or WLC to release the mobile device from the walled garden.
- The mobile device exits the walled garden: the mobile device is now abiding by the restrictions and configurations put in place by the MDM profile and is released from the walled garden.
MDM Profiles
MDM proiles are used for mobile device restrictions as well as globally configuring various components of a mobile device. MDM profiles can be removed from the device locally or can be removed remotely through the internet via the MDM server. MDM profiles can be locked down, and this is typically the case for company owned devices.
MDM Agent Software
Some mobile devices require MDM agent application software. Android devices are an example. An MDM agent application can report unique information about the Android device back to an MDM server. The MDM agent contacts the MDM server over the WLAN and is typically required to authenticate to the server. The agent then gives permission to the MDM server to make changes to the device.
Over the Air Management
Once a mobile device is enrolled, the management relationship is permanent as long as the profile exist. As long as the device has internet connectivity it can be managed by the MDM server. Communications between the MDM server and mobile device requires push notifications from a third-party service. When a push notification is received by the mobile device, it communicates back to the MDM server to get new configurations or messages.
Possible actions from MDM server over the Internet:
- Make changes to config
- Make changes to the device restrictions
- Deliver a message to the device
- Lock the device
- Wipe the device
- Make application management changes
Two types of remote wiping:
- Enterprise Wipe: basically returns the device to the state in which it was pre-profile
- Device Wipe: full device wipe, setting it back to factory defaults
Application Management
Once an MDM profile is installed on a device, all of the installed applications can be viewed from the MDM server. The MDM server can then whitelist or blacklist specific applications. This is common for corporate owned devices but not so much on employee owned devices. MDM solutions can also allow for integration with application stores like iTunes and Google Play in order to allow for access to public applications. Additionally applications can be pushed silently to devices.
Self Service Device Onboarding for Employees
The main purpose of a self-service device onboarding solution is to provide an inexpensive and simple way to provision employee personal WLAN devices onto a secure corporate SSID. The device onboarding solution provides a self-service method for an employee to configure the BYOD supplicant and install security credentials, such as an 802.1X/EAP root CA certificate. Onboarding solutions typically use an application that uses similar over-the-air provisioning aspects of MDM solutions to securely install certificates and WiFi client profiles onto mobile devices.
Dual-SSID Onboarding
Dual-SSID Onboarding is a process in which the employee initially connects to an open SSID, where they will be prompted with a captive portal. At this point they will need to authenticate through either the portal or a redirect link. Once validated they can disconnect form the open SSID and join the secured SSID.
Single-SSID Onboarding
Single SSID onboarding uses a single SSID that is capable of authenticating 802.1X/EAP-PEAP clients and 802.1X/EAP-TLS clients. The client logs in using 802.1X/EAP-PEAP connection using their corporate user/pass. They would then be sent to a captive portal, where they would sign in once again to validate they are allowed to onboard. Just like Dual-SSID, an onboarding program is downloaded to the device and executed, and then the application downloads the server certificate via SSL and provisions the supplicant on the device. Then the RADIUS server will initiate a Change of Authorization (CoA) to the employee device, disconnecting the devcie from the network. The device will immediately reconnect to the same SSID, using either 802.1X/EAP-PEAP or TLS, and then will validate the certificate.
MDM vs. Self-Service Onboarding
MDMs are typically the preferred choice for large corporations, giving them the ability to manage and monitor company WLAN devices as well as provide a provisioning solution for employee personal WLAN devices. Self-Service onboarding solutions are typically much cheaper and simpler to deploy.
Guest WLAN Access
A critical security concern with guest WLAN access is to ensure guests cannot gain access to the companies network infrastructure. At the very least, guests should be on a separate SSID, a unique VLAN, and have a guest firewall policy.
Guest SSID
Typically a guest SSID is open with a possible captive portal, where employee SSIDs are normally protected with 802.1X/EAP security. In some cases, enterprises will use encrypted guest access and provide data privacy using dynamic PSK. A guest SSID should never be hidden, and should have a simple name.
Guest VLAN
Guest user traffic should be segmented into a unique VLAN. If we are using guest firewall policies at the edge of the network, then isolating the guest VLAN in the DMZ is not necessary.
Guest Firewall Policy
Arguably the most important security component of a guest WLAN is the firewall policy which should restrict guests from getting near the company netowrk infrastructure and resources. Firewall ports that should be permitted are the DHCP server (UDP port 67), DNS (UDP port 53), HTTP (TCP port 80), and HTTPS (port 443). If VPN is required, then IPSec IKE (UDP port 500) and IPSec NAT-T (UDP port 4500) should also be permitted. If desired some vendors have built in the ability to do application layer firewall restrictions, banning apps like YouTube and Netflix.
Captive Web Portals
Guests often login via a captive portal, with the most important aspect being the legal disclaimer. A good legal disclaimer states what is acceptable behavior when using the guest WLAN. A captive portal solution effectively turns a web browser into an authentication service.
Captive Portal Steps:
- User connects to the WLAN and attempts to go to a web page.
- The user regardless of intended site, is redirected to a different URL, which displays a captive portal login page. Additionally IP redirect, DNS redirection, or redirection by HTTP can also be used.
Captive portals are typically customizable to include company logo, acceptable use policy, as well as configuring the login requirements.
Client Isolation, Rate Limiting, and Web Content Filtering
Client isolation usually means that packets arriving at the APs wireless interface are not allowed to be forwarded back out of the wireless interface to other clients. This helps prevent peer-to-peer attacks against other guests. This is highly recommended. Rate limiting can be used to curb traffic at either the SSID level or the user level. It can ensure that the majority of the bandwidth is preserved for employees. A web content filtering solution blocks employees from viewing websites based on content catagories.
Guest Management
A guest management server can be either cloud-based or reside as an on-premise server in a company data center. Modern WLAN guest management solutions offer robust report-generation capabilities for auditing and compliance requirements. Credentials can be delivered via an electronic wallet, SMS test message, an email message, or a printed receipt.
Guest Self-Registration
Simple self-registration pages allow guests to fill out a form and their guest account is created and displayed or printed for them. More advanced self-registration pages require guest to enter an email or SMS address, which is then used by the registration system to send users their login credentials.
Employee Sponsorship
Employee sponsorship requires the guest to enter the email of an employee who must approve and sponsor the guest. An email is typically sent to the employee with a link that allows them to accept or reject the guest request.
Social Login
Social login is a method of using existing login credentials from a social networking service (such as Twitter, Facebook, or LinkedIn) to register on a third-party website. Social login is often enabled using the OAuth protocol that allows access tokens to be issued to third-party clients by an authorization server. Retail and service businesses will often use this as a means of obtaining marketing information about their customers.
Encrypted Guest Access
A simple way to provide encryption on a guest SSID is to use a static PSK. It is not ideal due to brute-force dictionary attacks and social engineering attacks. Taking it a step further, some WLAN vendors offer cloud-based solutions to distribute secure guest credentials in the form of unique per-user PSKs.
Hotspot 2.0 and Passpoint
Hotspot 2.0 is a WiFi Alliance technical specification that is supported by the Passpoint certification program. The WLAN client device is equipped by a cellular carrier service provider with one or more credentials, such as a SIM card, username/password pair, or X.509 certificate.
Two main goals of the Hotspot 2.0 techinical spec:
- To make public/commercial WiFi networks as secure and easy to use as enterprise/home WiFi networks
- To offload 3G/4G cellular network traffic onto WiFi networks
Passpoint is the brand for the certification program operated by the WiFI Allliance.
Access Network Query Protocol
Passpoint devices use the Access Network Query Protocol (ANQP), a query and response protocol defined by 802.11u. An ANQP server is needed to respond to ANQP queries from Passpoint clients, and can be standalone or embedded in the APs.
ANQP is used by Passpoint mobile devices to discover a range of information, including:
- Venue name
- Required authentication types
- Information about 3GPP cellular networks available through the AP
- Roaming consortium (for hotspots with roaming agreements with other service providers)
- Network Address Identifier (NAI) home
- NAI realms accessible through the AP
- WAN metrics
- Much more
Passpoint clients use Generic Advertisement Service (GAS) query frames to gather most of the needed information from the ANQP server.
Hotspot 2.0 Architecture
The service provider components include:
- Online Sign Up (OSU)
- Subscription Remediation server (SubRem)
- Policy Server
- EAP and RADIUS
- Home Location Register server (HLR)
- Home AAA server
- Mobile Application Part (MAP)
- Certificate Authority (CA)
802.1X/EAP and Hotspot 2.0
Hotspot 2.0 supported client credentials and EAP Protocols
Credential Type EAP Method
-
- Client Certificate EAP-TLS
- SIM Card EAP-SIM
- VSIM Card EAP-AKA
- Username/Pass EAP-TTLS
EAP-Subscriber Identity Module (EAP-SIM)
EAP-SIM was primarily developed for the mobile phone industry, and more specifically for second-generation (2G) mobile networks. EAP-SIM, outlined in IETF RFC 4186, specifies an EAP mechanism that is based on 2G mobile network GSM authentication and key agreement primitives. EAP-SIM does not offer mutual authentication, and key lengths are much shorter than the mechanisms used in third-generation mobile networks.
EAP-Authentication and Key Agreement (EAP-AKA)
EAP-AKA is an EAP type primarly developed for the mobile phone industry and more specifically for 3G mobile networks. EAP-AKA, outlined in the IETF RFC4187, defines the use of authentication and key agreement mechanisms already being used by the two types of 3G mobile networks.
- Universal Mobile Telecommunications System (UTMS)
- CDMA2000
Encryption key lengths can be substantially longer, and mutual authentication has now been included. EAP-AKA can also be used in 4G moblie networks that typically use LTE.
Non-SIM Passpoint devices, like laptops, will use either EAP-TLS or EAP-TTLS security.
Online Sign-Up
Roaming Agreements
Simply put, a customer of one service provider may be able to also connect to a hotspot WLAN service of a different cellular provider with no additional cost. Passpoint enables inter-carrier roaming, with discovery, authentiation and accounting.
Network Access Control (NAC)
NAC evaluates the capability or state of a computer to determine the potential risk of the computer on the network and to determine the level of access to allow.
Posture
Posture is a process that applies a set of rules to check the health and configuration of a computer and determine whether it should be allowed access to the network. A key task of posture assesment is to verify that security software (antivirus, antispyware and a firewall) is installed, up-to-date, and operational. A posture check is performed by a persistent agent (software that is permanently installed on the computer) or by a dissolvable agent (software that is temporarily installed).
OS Fingerprinting
When a client establishes a layer 2 connection, the next action is to send a DHCP request to obtain an IP address. This requests different parameters under teh SHCP option 55 portion of the request. These parameters within option 55 create a fingerprint that can be used to identify the operationg system of the client. Another OS detection method is HTTP fingerprinting in which the user-agent header within an HTTP packet identifiies the client operating system.
AAA
Authorization is used to analyze information including:
- User type (admin, help desk, staff)
- Locatoin, connection type (wireless, wired, VPN)
- Time of day
- Device type (smartphone, tablet, computer)
- Operating system
- Posture (system health or status)
Authentication is about who you are, whereas authorization is about other parameters, such as what, where, when and how. Additionally, unlike authentication, where you are or are not authenticated, authorization varies depending on the parameters and the situration.
RADIUS Change of Authorization
RADIUS CoA can be used to dynamically change the permissions that the user has on the network.
Single Sign-On
Single Sign-On allows users within an organization to access many if not all of the internal resources using a single network login. Because many applicaitons started to migrate to the cloud, user logins had to extend outside the corporate network. This authentication can authorization across organizational boundaries introduces more complexity and greater security risk. This lead to the use of two technoligies, Security Assertion-Markup Language (SAML) and OAuth, which provided the access security needed to expand outside the organizations network.
SAML
SAML provides a secure method of exchanging user security information between your organization and an external service provider. Instead of requring the user to login, a trust relationship between your authentication server and the cloud application will validate the users identity and provide access to the application or service.
3 roles for SAML specification for the SSO process:
- The identity provider (IdP) – asserting party
- The service providcer (SP) – relaying party
- The user
OAuth
It is different from SAML as it is an authorization standard and not an authentication standard. WIth OAuth, a user logs in to the authentication application. Once logged in, the user (resouce owner) can authorize a third-party application to access specific user information or resources, providing an authorization flow for web and desktop applications, along with mobile devices.
Chapter Review
In CWNA Chapter 18, BYOD (Bring Your Own Device) was the focus. In today’s world, every person has at least one if not more personal device with them at all times. A quick google search netted the average person has 1.7 devices for work. That is a huge issue for security as we have mentioned and handling that is of the utmost importance. We discussed how MDM plays a huge role in doing just that, along side the security measures that are deployed to ensure those devices only have access to the network resources deemed appropriate by the corporate IT administrators. Additionally we discussed ways in which guests can join the network and how to secure against access to the corporate network as well as other guest clients. Lastly we touched on what Hotspot 2.0 and Passpoint can offer us. Our next chapter will be CWNA Chapter 20 as CWNA Chapter 19 802.11ax is not tested on the exam. Since we are here to pass the exam and not waste time, focusing on that right now is something we can do after we are CWNAs.
Interesting Link of the Day
Today I wanted to mention the new Cisco 9105AX series access points. There are two models in this series, the 9105i and the 9105w. Both are 802.1ax with the 9105i setup as a ceiling mounted small form factor AP requiring a smaller bracket than your conventional Cisco APs. The 9105w is a wall mounted AP designed for hospitality, residence halls and other residential type locations. The pictures below were sourced from wireless engineer Dave Benhams blog. Check out his post HERE.


















